In this article, I
will be describing you the steps on how to access the Azure Functions that is
configured to not allow anonymous access from Logic App through AD
authentication.
Prerequisites:
- Azure Functions https://docs.microsoft.com/en-us/azure/azure-functions/
- Azure Logic App https://docs.microsoft.com/en-us/azure/logic-apps/
- App Registration https://docs.microsoft.com/en-us/azure/active-directory/develop/
Also make sure you
have sufficient access (Like "Contributor" rights in Azure Resource
Group also "Owner" rights at Resource level) to create all the above
azure artifacts
First let us begin
by creating Azure functions.
Go to Azure Portal
and create a resource. Select Azure Functions.
Create the Function
App with all necessary details from drop down.

Select the Storage account in the same region also choose the plan type appropriately based on the usage/budget.

Finally validate the
properties and create the Function App.

Add a function and
choose the Template (I have chosen Http trigger: which gets triggered manually
when you try to access from any client application) and finally create
Function.



Once you have
created a sample application, navigate to the Azure Function-> "Code +
Test".
The below sample
template accepts the Json request and sends response in string.

You can test it out
by using "Test/Run" with sample Input and click Run:
{
"name":"John"
}

The
response you would receive is :

This
can be tested even through the Postman.

Now, let's to
restrict Azure functions to not allow with anonymous user and give a try to
access the Azure Functions through Postman.
Goto
"Authentication and Authorization"under Function App blade then turn
on "App Service Authentication" under "Access Restrictions"
section.
Also choose
"Login with Azure Active Directory" under "Action to take when
request is not authenticated "and finally Save.

This particular
setting will not allow the Azure function to respond unless it is authenticated
through Azure Active Directory.
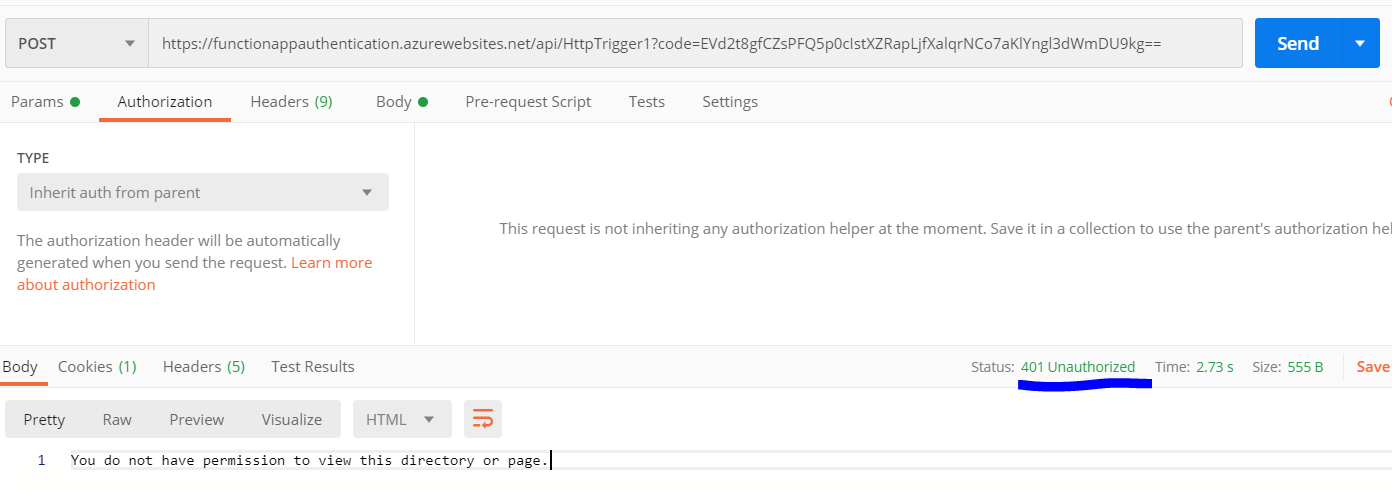
Postman will throw
an error with code 401 as shown below.
Now this function
can be accessed through AD Authentication. To authenticate we must first
register the Application using App registration.
We can do this App
registration directly creating the Azure AD App via Azure Function
"Authentication / Authorization" blade.
For that we have to
choose "Azure Active Directory" option in "Authentication /
Authorization" blade and finally create a new AD App by providing the
appropriate App name in Create App field as shown below.
These options can be
viewed under Express mode as shown in the below screenshot.
Express mode allows
user to create an AD Application or select an existing AD application in your
current Active Directory.

However, I recommend
you to create App Registration manually . If you are building an application
for external users that will be distributed by Microsoft, you must register as
a first party application to meet all security, privacy, and compliance policies.
Let us create App
Registration.
Go to App
registration and create AD App.

Create Secret by
choosing "Certificates & Secrets" in the left pane of the App
registration.

Copy
the secret and keep it ready to use it in Logic App.

Also, please copy
the Client ID , Tenant ID and keep it ready to use it in Logic App later.

Now we will have to
choose the particular AD Application in Azure functions via which an user can
access.
Goto -> Azure
Functions-> choose the Azure Function-> Select "Authorization /
Authentication" -> choose "Azure Active directory" in the
right pane.
Select already
created AD App "functionappaccess" by verifying the Client ID and
finally "OK"


Later Save the
Authentication / Authorization configuration.
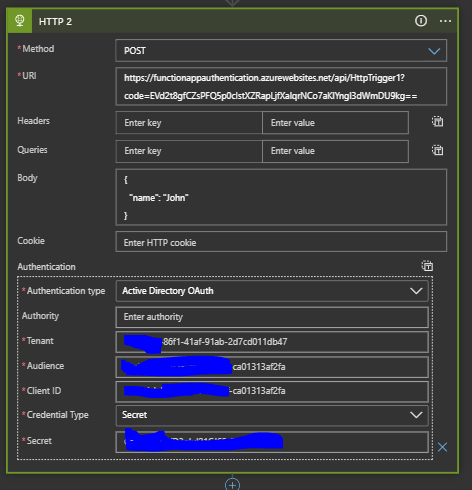
Now it is time to
test the Authenticate with Secret, ClientID , TenantID in Logic apps.
Create a Logic App
may be either with Recurrence Trigger or Manual Http Trigger.
Later create Http
action with TenantID, Client ID and the Secret.
Please note I have
used ClientID for Audience.
Please give a try by
running it manually.
Result:


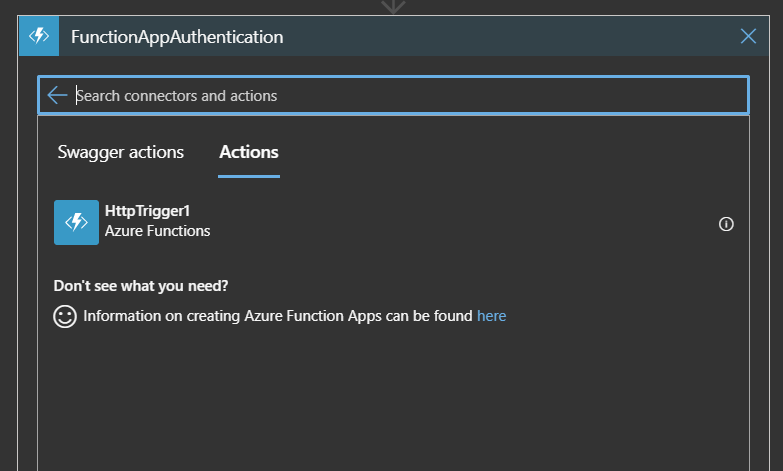
The Azure Functions
can also be reached by Azure Functions actions.
Add Azure Function
action-> Function-> Choose the
action
Please give a manual
run for testing.
Result :

Please give a manual
run for testing.
Result :


Similar approach can be taken to access Azure Web Apps using AD Authentication.
Thanks for going
through the article. Hope you enjoyed it!
Please leave your
comments/queries in the comments section.
In this article, I
will be describing you the steps on how to access the Azure Functions that is
configured to not allow anonymous access from Logic App through AD
authentication.
Prerequisites:
- Azure Functions https://docs.microsoft.com/en-us/azure/azure-functions/
- Azure Logic App https://docs.microsoft.com/en-us/azure/logic-apps/
- App Registration https://docs.microsoft.com/en-us/azure/active-directory/develop/
Also make sure you
have sufficient access (Like "Contributor" rights in Azure Resource
Group also "Owner" rights at Resource level) to create all the above
azure artifacts
First let us begin
by creating Azure functions.
Go to Azure Portal
and create a resource. Select Azure Functions.
Create the Function
App with all necessary details from drop down.
Select the Storage account in the same region also choose the plan type appropriately based on the usage/budget.
Finally validate the
properties and create the Function App.
Add a function and
choose the Template (I have chosen Http trigger: which gets triggered manually
when you try to access from any client application) and finally create
Function.
Once you have
created a sample application, navigate to the Azure Function-> "Code +
Test".
The below sample
template accepts the Json request and sends response in string.
You can test it out
by using "Test/Run" with sample Input and click Run:
{
"name":"John"
}
The response you would receive is :
This
can be tested even through the Postman.

















Similar approach can be taken to access Azure Web Apps using AD Authentication.
Thanks for going through the article. Hope you enjoyed it!
Now, let's to
restrict Azure functions to not allow with anonymous user and give a try to
access the Azure Functions through Postman.
Goto
"Authentication and Authorization"under Function App blade then turn
on "App Service Authentication" under "Access Restrictions"
section.
Also choose
"Login with Azure Active Directory" under "Action to take when
request is not authenticated "and finally Save.
This particular
setting will not allow the Azure function to respond unless it is authenticated
through Azure Active Directory.
Postman will throw
an error with code 401 as shown below.

Now this function
can be accessed through AD Authentication. To authenticate we must first
register the Application using App registration.
We can do this App
registration directly creating the Azure AD App via Azure Function
"Authentication / Authorization" blade.
For that we have to
choose "Azure Active Directory" option in "Authentication /
Authorization" blade and finally create a new AD App by providing the
appropriate App name in Create App field as shown below.
These options can be
viewed under Express mode as shown in the below screenshot.
Express mode allows
user to create an AD Application or select an existing AD application in your
current Active Directory.

However, I recommend
you to create App Registration manually . If you are building an application
for external users that will be distributed by Microsoft, you must register as
a first party application to meet all security, privacy, and compliance policies.
Let us create App
Registration.
Go to App
registration and create AD App.
Create Secret by
choosing "Certificates & Secrets" in the left pane of the App
registration.
Copy
the secret and keep it ready to use it in Logic App.
Also, please copy
the Client ID , Tenant ID and keep it ready to use it in Logic App later.
Now we will have to
choose the particular AD Application in Azure functions via which an user can
access.
Goto -> Azure
Functions-> choose the Azure Function-> Select "Authorization /
Authentication" -> choose "Azure Active directory" in the
right pane.
Select already
created AD App "functionappaccess" by verifying the Client ID and
finally "OK"
Later Save the
Authentication / Authorization configuration.
Now it is time to
test the Authenticate with Secret, ClientID , TenantID in Logic apps.
Create a Logic App
may be either with Recurrence Trigger or Manual Http Trigger.
Later create Http
action with TenantID, Client ID and the Secret.
Please note I have
used ClientID for Audience.

Please give a try by
running it manually.
Result:


The Azure Functions
can also be reached by Azure Functions actions.
Add Azure Function
action-> Function-> Choose the
action

Please give a manual
run for testing.
Result :

Please give a manual
run for testing.
Result :


Similar approach can be taken to access Azure Web Apps using AD Authentication.
Thanks for going through the article. Hope you enjoyed it!
Please leave your
comments/queries in the comments section.


